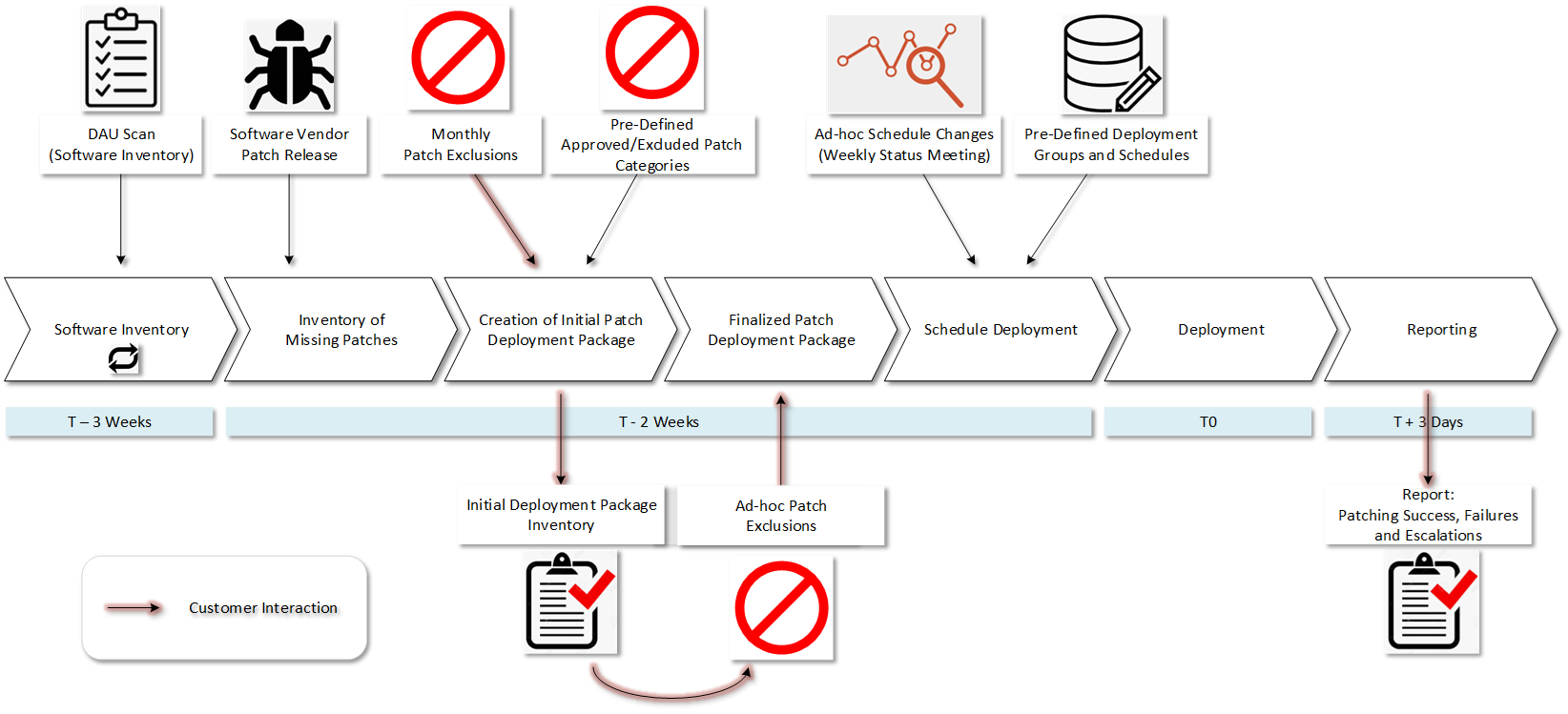
Patching is a crucial component of maintaining network stability and security, and not doing so leaves you at a significant risk of being a victim of ransomware. Unfortunately, many IT departments struggle to patch effectively, or in some cases completely ignore it. During patching, issues such as deployment failures, application incompatibilities, outages, and reboot failures can occur. However, these setbacks should not deter a company from continuing future patching processes. It is necessary that an efficient patching process is established before it is too late.
In an article by ZDNet, they state, “Over half of the most common security vulnerabilities exploited by criminals to conduct cyberattacks and distribute malware are more than a year old, and some are over five years old, demonstrating how failure to apply security updates is leaving organisations vulnerable to hacking and malicious compromise.” The unfortunate part is that “There are patches from vendors to fix all of these bugs, but software patching is often forgotten or ignored by companies and individuals.” They suggest that, “The most effective thing that can be done to protect networks from falling victims to attacks that use these vulnerabilities is to ensure all products – particularly Microsoft ones – are up to date and that if a new security patch is released, to apply it as soon as possible.”
Cybercriminals have an abundant selection of vulnerabilities to advantage of, here are some examples of the most exploited ZDNet listed out:

- CVE-2018-15982 – Adobe Flash Player
- CVE-2018-8174 – Microsoft Internet Explorer
- CVE-2017-11882 – Microsoft Office
- CVE-2018-4878 – Adobe Flash Player
- CVE-2019-0752 – Microsoft Internet Explorer
- CVE-2017-0199 – Microsoft Office
- CVE-2015-2419 – Microsoft Internet Explorer
- CVE-2018-20250 – Microsoft WinRAR
- CVE-2017-8750 – Microsoft Internet Explorer
- CVE-2012-0158 – Microsoft Office
Click here to read the full article by ZDNet.
If you would like to learn more about the importance of software patching, then click here to read our blog.